AI, deepfakes and phishing
SmartBrief - Marketing
MAY 1, 2024
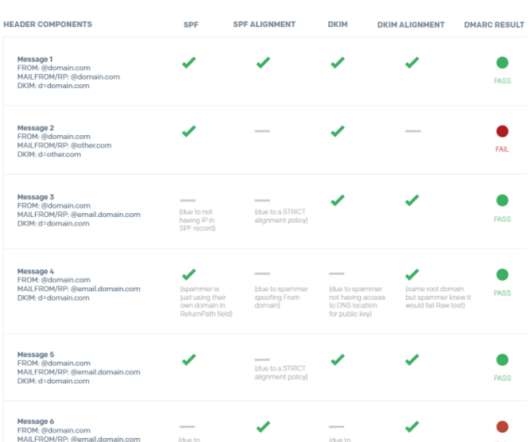
AI is adding a whole new dimension to phishing – and while many people are alert for suspicious phrasing or email addresses, fewer think to doubt the evidence of their own eyes. The post AI, deepfakes and phishing appeared first on SmartBrief. Voice, text and images AI scams don’t have to involve video.
















































Let's personalize your content