Advanced Tips for Protecting Your Small Business Network on a Budget
Webbiquity
JANUARY 21, 2020
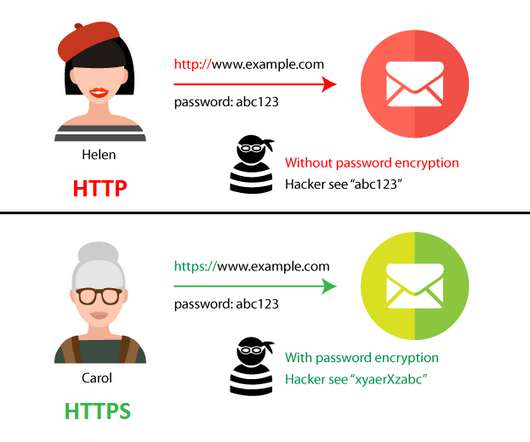
Your daily to-do list likely includes an array of tasks, from producing video marketing to working out ways to drive more traffic to your website. Advanced Phishing Techniques. You may think you know what a phishing email looks like, and it’s true that some are easy to spot. Image credit: Jimmy Chan from Pexels.
















































Let's personalize your content