The 3 Most Important Steps to Prevent Email Spoofing And Phishing
SendX
MAY 24, 2021
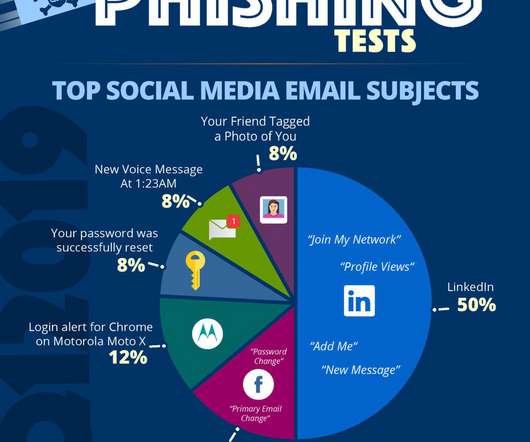
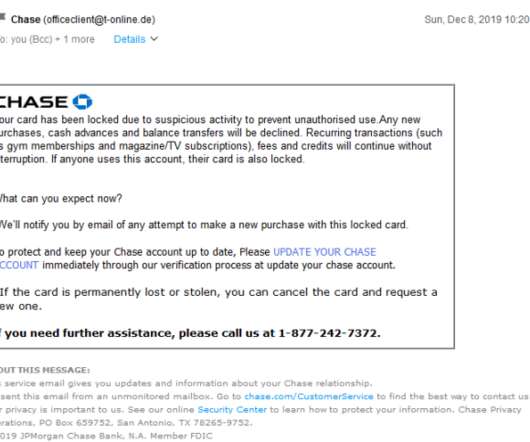
And out of all cyber incidents, 80% were made possible through phishing. That is why it is important to understand how to prevent email spoofing and phishing. What are Email Spoofing and Phishing? Email Phishing is accomplished through email spoofing (pretending to be a trustworthy source of email).













































Let's personalize your content