AI, deepfakes and phishing
SmartBrief - Marketing
MAY 1, 2024
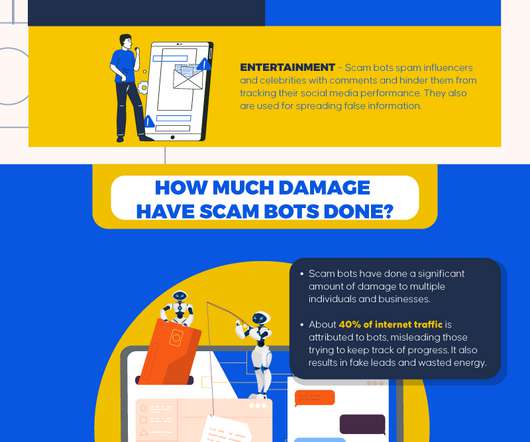
Now people are making their losses public, celebrities are speaking out about their digital impersonators and government agencies are considering harsher measures to fight the rising tide of AI-powered security hazards. The post AI, deepfakes and phishing appeared first on SmartBrief.














































Let's personalize your content