Social Media Hacking: How to Protect Your Account
Oktopost
DECEMBER 19, 2022
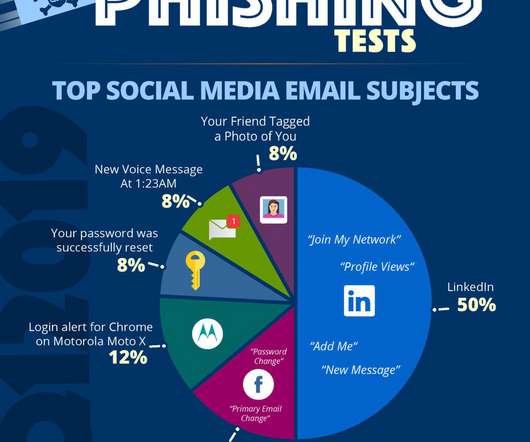
In this article, we’ll discuss the most common social media security risks, along with best practices to protect your social media accounts from hackers. Phishing Attacks. 9 Best Practices to Protect Social Media Accounts from Hackers. Phishing Attacks. 9 Best Practices to Protect Social Media Accounts from Hackers.

































Let's personalize your content