How Demandbase Is Evolving Past Third-Party Cookies
Engagio
MAY 31, 2021
What other account-based vendors in our space won’t tell you is that the deprecation will also impact account identification and the collection of intent behaviors. Additionally, they deploy email signature spyware to compare website visitor IPs with the email opener’s email domain. Intent Data Collection Without Third-Party Cookies.

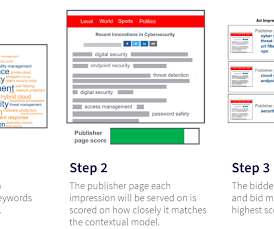













Let's personalize your content