Almost 60% of marketers haven’t implemented AMP, see why (and why it’s no excuse)
Unbounce
FEBRUARY 13, 2019
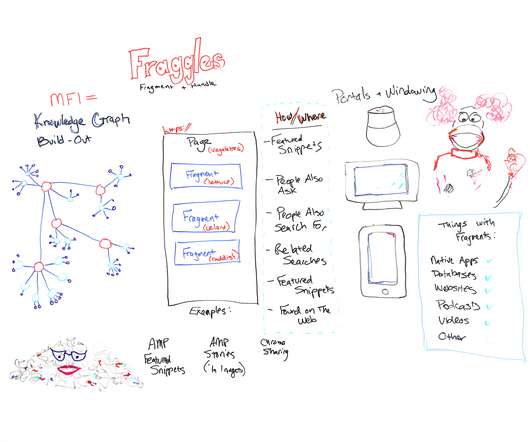
Essentially, AMP is a Google-backed framework for creating web pages that deliver near-instant load times, even on mobile. Google’s past behavior has made some people wary of AMP. For now, it’s worth saying that each has some validity. Validation issues with AMP pages we did create (2% of respondents).








































Let's personalize your content