Sustainability, Business Agility, Unicorns and New Executive Orders – July in Review
Champion Communications
AUGUST 3, 2021
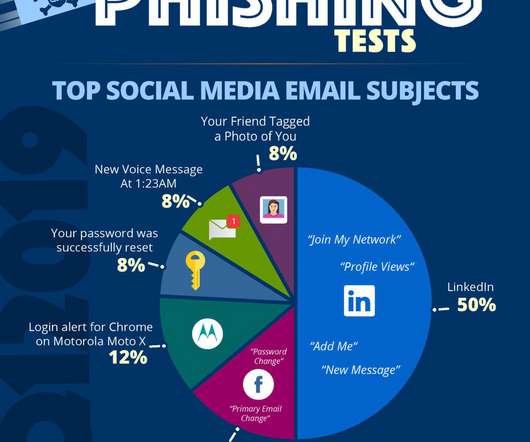
Even highly skilled IT professionals fall prey to phishing attacks . Remote working has made phishing attacks all too common. Anyone, regardless of experience or cybersecurity savvy, is susceptible to a phishing attack,” says Chris Goettl, Ivanti’s senior director of product management. Clear Junction. get in touch at:?













































Let's personalize your content