What is Cybersecurity? Your Guide to Digital Defense
Salesforce Marketing Cloud
DECEMBER 5, 2023
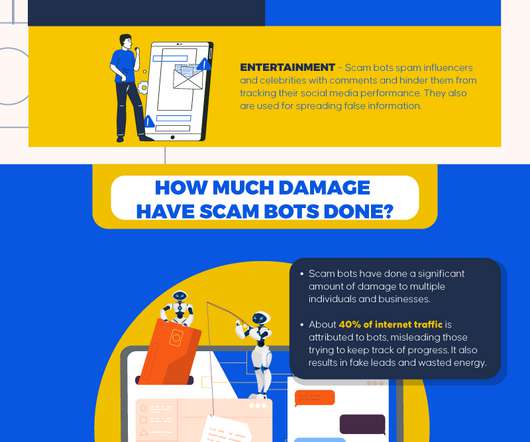
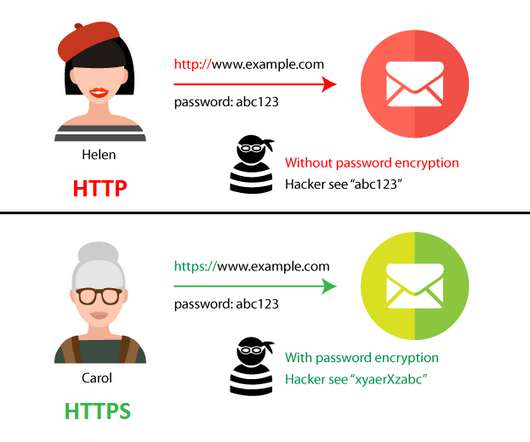
In fact, the three primary ways in which cybercriminals can access an organization are stolen credentials, phishing, and exploitation of vulnerabilities. Protect your brand reputation and customer trust in the market. While threats can indeed stem from cunning con artists, they also come from inadvertent employee errors.






































Let's personalize your content