Fraud Detection with Machine Learning and AI
Valasys
APRIL 25, 2024
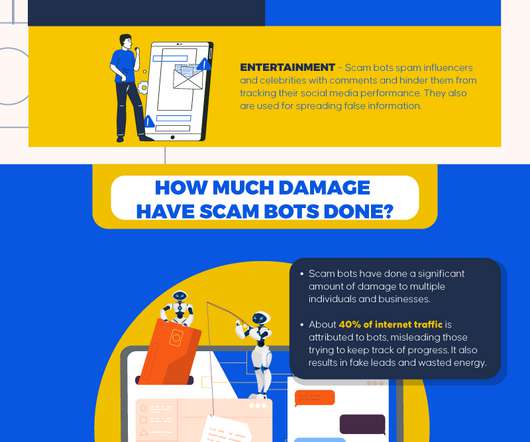
ML models are trained to identify patterns and detect fraudulent activities or any anomalies within the data. They are trained on standard patterns of billing amounts and medication prescriptions for various conditions. Improved Accuracy Intelligent machines using AI and ML algorithms are trained on a huge dataset.




























Let's personalize your content