15 (More) Fascinating Facts About Internet and Social Media Use in 2021
Webbiquity
AUGUST 3, 2021
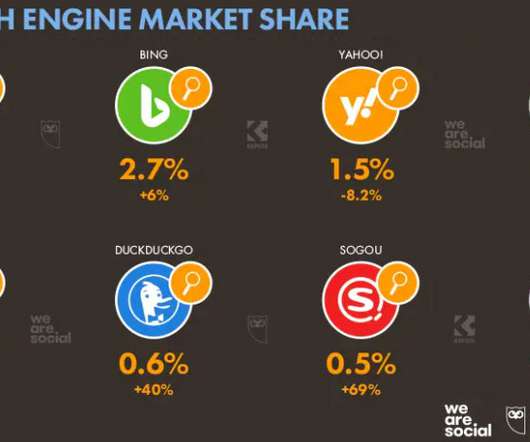
A recent post here detailed 12 Fascinating Facts About Global Internet Use in 2021 , compiled from that report. General Internet Use Statistics. 98% of Internet users (globally, aged 16-64) say they use conventional search engines (the other 2% likely didn’t understand the question). General Internet Use Statistics.



















Let's personalize your content