How Demandbase Is Evolving Past Third-Party Cookies
Engagio
MAY 31, 2021
Your company will still have access to first-party cookies on your own website, typically provided by your marketing automation platform. As of today, Demandbase processes over 20 billion raw identification signals per day. In reality, the announcement from Google is specifically referring to the deprecation of third-party cookies.

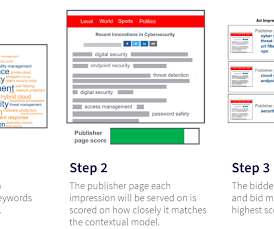

















Let's personalize your content