Social Media Hacking: How to Protect Your Account
Oktopost
DECEMBER 19, 2022
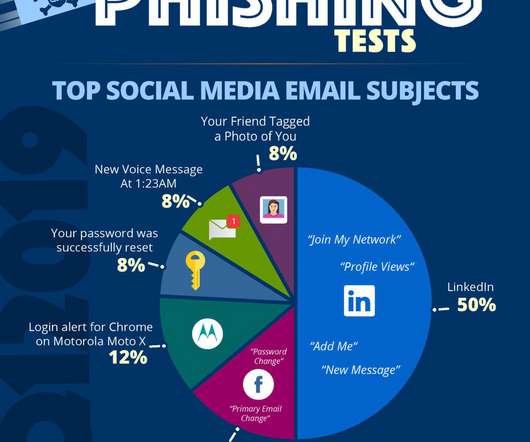
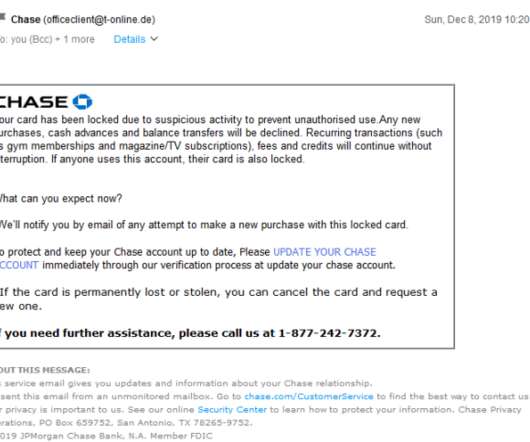
It’ll help you stay ahead of potential attacks and offer your B2B services that your customers can trust. Phishing Attacks. There are a few ways to mitigate the potential human error: Use a social media management platform with unique logins and permissions to prevent too much access to administrator privileges.




































Let's personalize your content