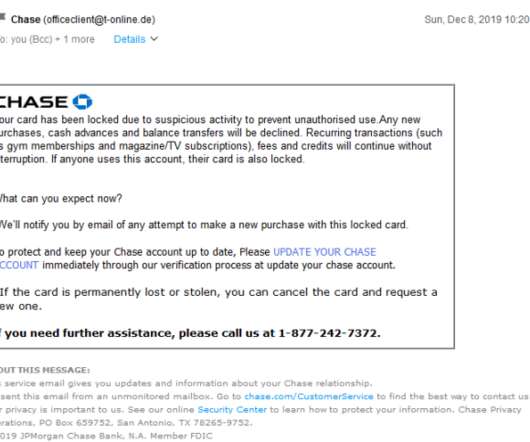
Our ESP has been hacked!
Goolara
JANUARY 23, 2020
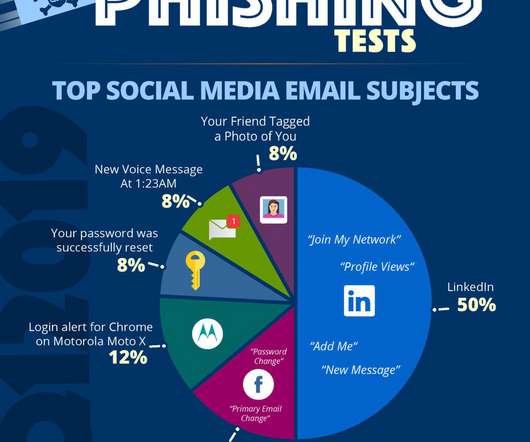
When email was created in the early 1970s, the designers had no idea how popular it would become or the range of problems that could be introduced. The use of this protocol will help prevent phishing emails (those pretending to be from eBay, Bank of America or other brands with good reputations) from landing in your inbox. Prevention.


















Let's personalize your content