5 Types of Data Breaches You Should Know About
Valasys
SEPTEMBER 11, 2020
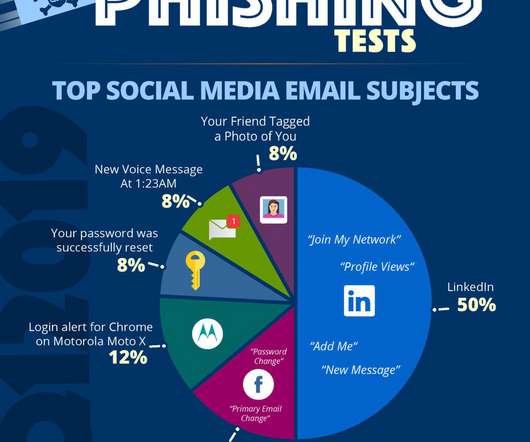
3) Phishing. Phishing is amongst the most common forms of email malware and amongst the foremost types of data breaches, worth mentioning. According to the Data Breach Investigations Report (DBIR) by Verizon, 70% of cyber attacks use a combination of phishing and hacking. 4) Denial of Service (DoS).





















Let's personalize your content