SaaS applications have a reputation for being unsecure but is that a fair statement? Any online software indeed has potential vulnerabilities because it exists on the internet. If you’re wondering how SaaS security works and how vendors can secure their applications, you just landed in the right place.
This article will explore the most proven working practices to secure SaaS web and applications. Let’s start by looking at what SaaS is, examining the SaaS security landscape, investigating some factors that make it insecure, learning about some popular SaaS attacks and threats, and then narrowing it down by checking SaaS security tips.
The Definition of IaaS, PaaS, and SaaS
IaaS, PaaS, and SaaS are common abbreviations you might have already encountered. They stand for Infrastructure as a service, Platform as a service, and Software as a service, respectively, and are essentially cloud computing services.
- Infrastructure as a Service (IaaS) offers a pay-as-you-go cloud-computing service that allows users to scale up and down quickly in response to various business needs and requirements.
- Platform as a Service (PaaS) refers to a cloud-computing model where a third-party service provider delivers software and hardware tools to you over the internet, usually for application development.
- Software as a service (SaaS) is an on-demand, readily-available cloud computing service. With SaaS, there is no need to install and maintain software since you can access the software on the internet.
Popularity of SaaS
SaaS is the most popular and widely used cloud-computing model. Indeed, the adoption of SaaS continues to explode, and statistics and figures seem to fully concur with this fact. According to the 2021 State of SaaSOps reports, businesses use an average of eighty IT-sanctioned SaaS applications, representing a five-times increase from 2015. And this trend does not show any signs of stopping as more and more organizations continue to invest in SaaS. According to Gartner’s 2020 I&O Leaders Survey data, 70% of global enterprises are continually investing in SaaS services and will continue to do so. You can imagine what this trend does to the SaaS market. A graph extracted from Statista shows the SaaS market's previous, present, and future growth.
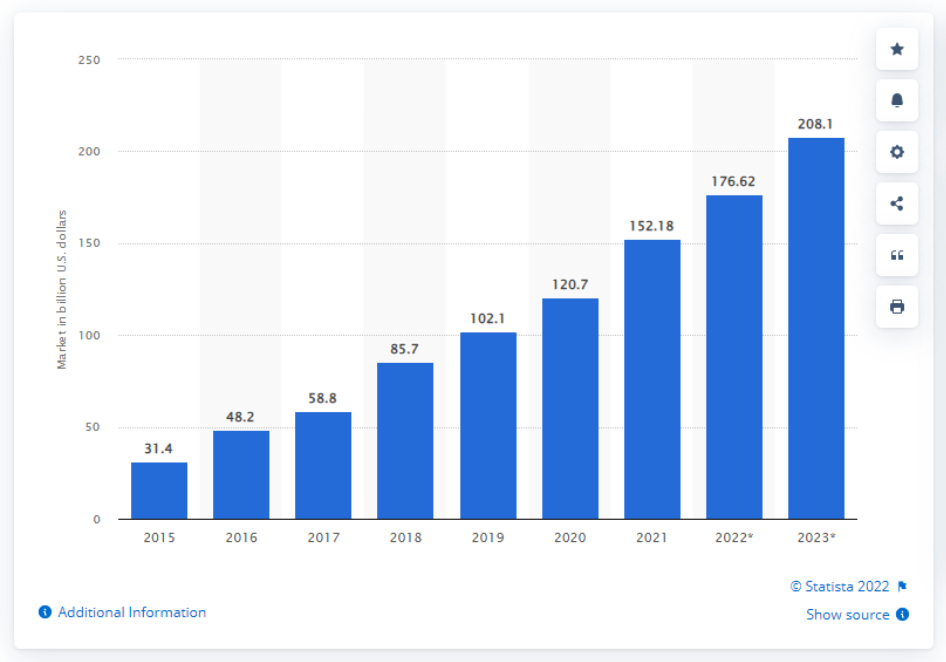
SaaS end-user spending worldwide from 2015 to 2023
What is SaaS Security?

SaaS security refers to all the measures, policies, practices, and tools laid down by the SaaS providers to safeguard data privacy and ensure the safety of all resources and assets contained therein. In short, SaaS security policies are meant to ensure the security and trustworthiness of SaaS web applications.
SaaS is less Secure — A Myth or a Fact?
Is SaaS less secure and less robust? This is a common question that usually comes from people who believe in the myth that SaaS is more vulnerable to security threats than on-premise applications.
Although we have seen reports from Google that portray SaaS as insecure, technical issues and hitches portrayed by SaaS are not enough proof that the service is insecure. For your information, these problems are usually rare. Moreover, no major SaaS compromise has been documented to date.
Even though SaaS is secure, that doesn’t mean that these applications are not susceptible to vulnerabilities. As a matter of fact, cybersecurity risks are still a major concern for SaaS users, and measuring the risks is an even bigger problem.
What Makes SaaS Apps Risky?
At this point, you are probably yearning to know the factors that will make SaaS applications vulnerable to security threats. The factors are explained below;
Virtualization
Virtualization continues to dominate cloud applications, and it is only safe that we look at it as a double-edged sword. You can look at virtualization as utilizing the physical hardware in running several standalone resources like servers and networks. But imagine what could happen if one of the servers is compromised. Whereas virtualization technology has undergone a significant revolution that seeks to improve network efficiency, it is an element that hackers prefer as a stepping stone toward the entire network. But it could still be an enormous asset when configured with security in mind.
SSO Risk
The single Sign-On is a popular and productive SaaS tool that possesses the unique ability to streamline access to cloud-computing services using only one user authentication and thereby improving user experience. With SSO, employees only use one set of credentials to access cloud-based web applications. However, SSO is more concerned with enhancing user access and not restricting it makes it a risk to SaaS security. Once an attacker succeeds in accessing the initial SSO account, they also gain access to all the linked data and resources.
Cloud Services Standards
The security of Software as a service is directly influenced by the provider’s maintenance standards. And as you would probably guess, not all providers adhere to the internationally accepted SaaS security standards. Finding a provider claiming to be compliant but without a SaaS-specific certification is not hard. Such providers are more likely to compromise the entire security of the SaaS applications.
Data Control
All clients’ data is hosted in the clouds meaning that clients lack total control over their data. So, clients fall at the mercy of SaaS providers if things go south. Also, because the clients lack total control over their data, it is hard for them to establish who had access to it and some of the scenarios that could imply compromised data. And these questions gain more if the data stored is too sensitive.
Universal Access
One of the things that make SaaS applications more enticing is the fact they can be accessed anywhere and anytime. This feature might look like a good thing, but it could have its own security risks. For instance, accessing the application over WiFi and with no virtual private network automatically renders the application vulnerable to attacks. As such, if the access points are not secure, hackers will have an easy time accessing the application.
Obscurity
As a client, it would be best to understand in detail how everything works. However, clients often lack the technical know-how about how the SaaS provider handles their data. Such obscurity should be considered a red flag to the security of your data. A good SaaS service provider should be as transparent as possible. For instance, they should clearly spell out their backend process, among many other aspects. After all, clients have the right to know how their data is stored and handled by SaaS providers.
SaaS Security Risks and Threats
Now that you understand what causes SaaS insecurities, it is time to look at some top security threats. The following are the top security risks and risks your organization could be vulnerable to when using SaaS applications and services.
Malware Infection
Malware infections have been increasing more so in the recent past, and attackers seem to be shifting their attention to SaaS applications. But one would wonder where SaaS malware infection comes from. Poor cybersecurity measures can later result in DDoS attacks, where the cybercriminals target the entire system, servers, and devices.These devices are home to some of the most dangerous infections. Users who use such endpoints to access data only make the data more vulnerable to malware infections.
Ransomware Attacks
Ransomware is a unique form of malware attack that puts SaaS data at great risk. Such malicious attacks are a big threat to the security of your data. For instance, in August 2021, researchers detected a novel and sophisticated ransomware variant called DeepBlueMagic that possessed a unique ability to disable security tools and remain undetected. Such malware strains emphasize the importance of SaaS protection. The fact that DeepBlueMagic could infiltrate computers running on Microsoft Windows servers and disable all security software means that it had the power to bring down SaaS applications.
Cloud Leaks
SaaS services are also vulnerable to cloud leaks. A cloud leak refers to a situation where the sensitive data of a business is accidentally exposed on the internet. Sensitive data could include things like credit card information, user personal details, and health records. Clients’ data in SaaS pockets is usually stored in unencrypted formats. If the leaked data lands in the hands of the hackers, things could be devastatingly bad as they will use such data for malicious reasons. Here are some examples of the notable cloud leaks that have occurred;
- The Verizon partner nice systems case in which six million customer records were exposed
- RNC Vendor data root analytics case that left 198 million voter records exposed on the internet
- The case where Allen Hamilton, a government contractor, left geospatial data and credentials exposed
Although these examples are not directly related to SaaS cloud leaks, they are a perfect demonstration of how bad things can be with cloud leaks.
OAuth Phishing Attacks
OAuth has grown in popularity to become one of the vastly applied open standard protocols in which users have the option to allow the usage of applications or websites on other applications. An OAuth phishing attack occurs when a hacker develops a new malicious and rogue application or website that masquerades as a well-known and used application. For instance, the malicious actor can use a compromised Office 365 to create an application that appears genuine but is on a mission to do evil. The threat actor will then trigger the victim to give permission to the malicious website or application. Once the victim approves the permission request, an OAuth token will be issued to the malicious application and do all sorts of harm, such as granting the attacker access to client resources such as email accounts and contact lists, among many others.
Brute Force Attacks
Because SaaS uses the Single Sign-On technique, some attackers will try to use all forms of attacks to bypass the SSO and access valid accounts. And the most dominant technique they use is the brute force attack. A brute force attack is where attackers guess several passwords and username combinations, hoping one of the guesses will be successful.
Compromised SSOs could be the key that opens doors to sensitive data and other resources, and hackers will be willing to go the extra mile to achieve it. Hackers mainly use the brute force attack technique because of its proven efficiency. Take an example of Microsoft Azure, a cloud computing platform that offers PaaS, IaaS, and SaaS. According to Microsoft, over 25 billion brute force attack attempts were blocked on Microsoft Azure.
- Malicious Third-party Extensions and Application add-ins
Application add-ins and web extensions are trendy among businesses. They are significant because they help to enhance user experience and improve application functionality. However, not all extensions and add-ins should be trusted because threat actors use them to infiltrate applications. It is, therefore, crucial to be keen when using third-party extensions. It would be best to ascertain the vendor’s identity to ensure they are genuine and not hackers who might be after your resources.
Best Practices To Secure SaaS Applications

The big question that we should now seek to answer is how one can secure SaaS applications from the security threats and attacks mentioned above. There are many security tricks, tips, and techniques to do so. This last section will explore the top seven measures you can apply to protect your SaaS applications against such threats.
End-to-End Encryption
The first and perhaps most significant security measure to protect SaaS applications is enabling end-to-end encryption. You notice that we have been mentioning data a lot in this article. Encryption helps to secure data from being accessed by unauthorized parties. To initiate the encrypted sessions, you must purchase an SSL certificate. In a market filled with excellent and versatile certificates such as Sectigo SSL, Comodo SSL, DigiCert SSL, Comodo Positive SSL Wildcard certificate, one has no explanation for the lack of an SSL certificate. Most people know SSL certificates as tools for securing in-motion data. But end-to-end encryptions are also available for motionless data like those stored in the SaaS platforms.
Conduct Regular Vulnerability Testing
It is common for SaaS providers to make high remarks about their products and how secure they are. However, their word should never be final. It would be best to do your due diligence to ascertain that the product is secure. And there is no better way to check SaaS security other than using the vulnerability testing technique. There are several ways to conduct vulnerability testing on your SaaS security. You can hire an expert to do the heavy lifting or use automated tools. Here is a comparison table of some of the best SaaS security tools that will be of great essence.
|
SaaS Tool |
Offerings |
Key Features |
|
Astra Pentest |
Regular threat assessment Manual penetration testing Compliance aid |
|
|
Intruder |
Vulnerability scanning (both internal and external) Regular penetration tests |
|
|
Detectify |
Web application scanning Application surface monitoring |
|
|
Acunetix |
Web application security scanner |
|
You must also fix the vulnerabilities as soon as they have been pointed out. In doing so, you will close all possible entry points that a hacker could leverage.
-
Conduct An Extensive Security and Awareness to all Employees
It is quintessential to educate all employees and stakeholders about SaaS security. The training program will be used to equip them with adequate knowledge about SaaS security and its implications and expose them to some of the attacks that SaaS applications are vulnerable to. The employees should be educated on how to spot SaaS security threats and the best measures to deal with such threats. Additionally, the training program will provide a unique avenue to warn malicious employees against insider threats and also create a cybersecurity culture in the organization.
Enhanced User Authentication
Examining how users access SaaS products is a fundamental security procedure you should never overlook. However, since cloud service providers usually handle authentication differently, it could prove a much more complicated process. For instance, some cloud service providers, such as Active Directory, OpenIDConnect, and Assertion Markup, have the option where clients can integrate with identity providers, while some do not. Similarly, some providers might give the users the option of two-factor authentication, while others might overlook this option.
Security experts must understand the services that are in use and the authentication options available. Tying Single Sign-On to AD (where possible) could go a long way toward ensuring robust authentication for the users. Users should also be encouraged to stick to best password practices and employ the two-factor authentication process where possible.
Apply the Least Privileges Principle
The principle of the least privileges is applied widely in information security, and it remains of great relevance and significance to SaaS products. According to the principle, different user categories should be attached to specific and different privileges. For instance, only admins should be allowed to access crucial files and folders. If a user has no business with certain resources or files, they should not be allowed access to those files.
Use a Virtual Private Network and Virtual Private Cloud
Virtual private networks are crucial where remote access to SaaS applications is needed. VPNs and VPCs will allow users to log in to their accounts from anywhere without serious traffic interception risk. The virtual private network will create a safety tunnel between the user's computer and the VPN server, hiding users’ activity and resources from external forces.
Complying With Local Policies and Guidelines
Depending on your geographical location, you and your clients are bound to certain regulations and policies, such as Payment Card Industry Data Security Standard (PCI/DSS) or the California Consumer Privacy Act (CCPA). Such standards are out to ensure the highest level of data security, and adhering to them could help boost SaaS security. Complying with regulations could be a smart approach to win clients’ trust.
Final Words
Like all internet elements, SaaS is vulnerable to security threats. These threats have devastating repercussions for the users and must be addressed exhaustively. This article has covered several aspects of SaaS security, such as the definition, causes, SaaS security threats, and the best measures to protect SaaS applications against those threats.
Roketto Team
Who the heck is "Roketto Team"? Great question! We use this authorship from time to time for guest writers and previous authors are no longer affiliated with the Roketto brand. What about the cute little rabbit in the Roketto Team avatar? That's Piko, our loveable, space travelling mascot. If this is your first time seeing him, don't worry, it won't be your last. He likes to turn up throughout Roketto's website and content, always looking to help our audience with their marketing needs.
















2.png)
2.png)




