The New Email Deliverability Rules: How to Make Sure You Reach Your Gmail and Yahoo Subscribers
Litmus
NOVEMBER 27, 2023
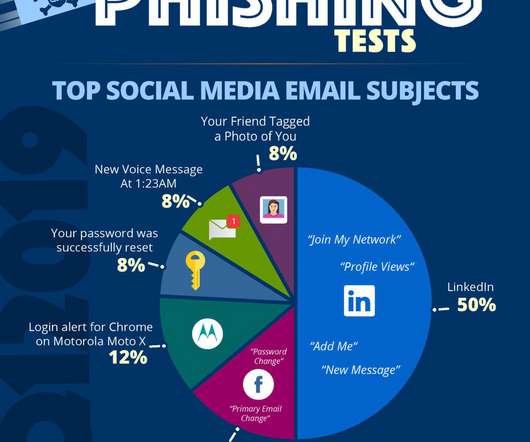
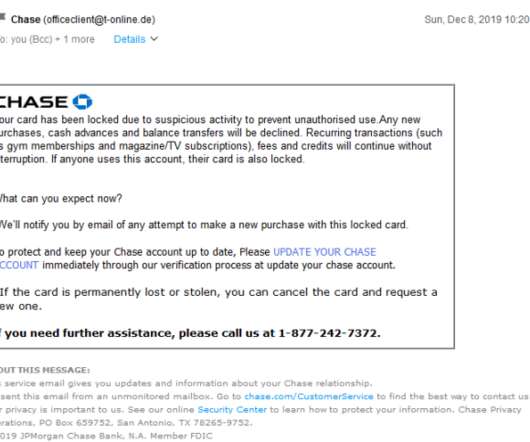
Google and Yahoo partnered in this effort to reduce the risk of phishing, spam, and malware. Writing, designing , and testing your email campaigns is overwhelming enough. On the contrary—to maintain healthy email deliverability, you must: Avoid emailing people without permission and purchasing email databases.































Let's personalize your content