I spent several frustrating hours this weekend trying to recover from a nasty virus that has hit WordPress installations on Network Solutions and Go Daddy, which is my hosting service. After wasting many hours fiddling with wp-config files and backing up and restoring databases, I hit upon a simple solution this morning that appears to have restored my three blogs to their former glory. Maybe it will help you.
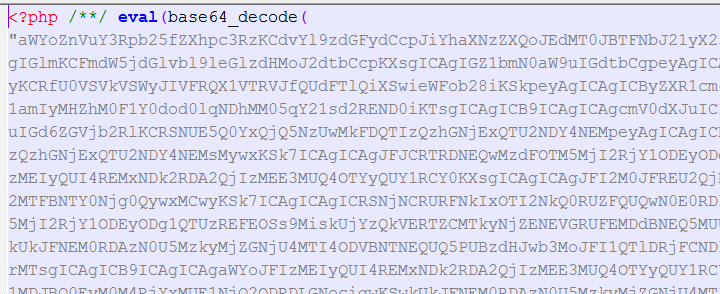
This virus is characterized by the insertion of a long string of seemingly random characters at the beginning of PHP files like the one depicted below. These files are scattered all over your WordPress directories and there’s no telling how many have been infected. You need to remove the malicious code from every PHP file to restore your system, and there could be hundreds of files.
First, the disclaimers: I’m not a programmer and I can’t guarantee that this solution will eradicate the virus once and for all. It’s possible that the creeps who developed it have hidden code somewhere to resurrect it at a later point, so I will post an update few days from now. Also, you should back up your database before attempting any recovery. It’s probably also a good idea to back up the infected files to a safe directory on your computer in case something goes wrong.
That said, here goes. This fix is for Windows, but the Mac version should be pretty similar:
1. You’ll need to download and install two open-source programs –Filezilla and Notepad++ – before you get started.
2. Open Filezilla and connect to the FTP server where your WordPress installation is located.
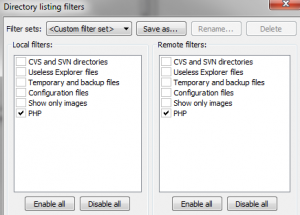
3. Now you’re going to create a filter in FileZilla to download and upload only PHP files. This will save you a lot of time because you won’t be sending large image and audio files back and forth. Go to “View –> Filename filters..” and choose “Edit filter rules…” Create a new rule called “PHP” or whatever you want. In the “Filter conditions:” drop-down menu, select “Filter out items matching none of the following.” In the space below that, choose the drop-down menus “Filename” “contains” and type “php” into the box. See screen grab below.
4. Then – and this is important – uncheck the box that says “Filter applies to: Directories.” If you don’t uncheck this box, FileZilla will only download files in the root folder and miss all the sub-folders. Click OK.
5. Back in the “Directory listing filters” dialog box, check the boxes next to your new PHP filter name in both the “Local filters” and “Remote filters” columns. Click OK. Your file transfer filter is ready.
6. In the “Local site:” window on FileZilla, create an empty directory on your computer where you can store the PHP files you download. In the “Remote site:” window, navigate to the directory containing your blog. This will be the one with the folders called wp-admin, wp-content and wp-includes. You actually won’t see those folders at the moment because your filter is on. If you want to check, temporarily disable the PHP filter to be sure you’re in the right directory.
7. In the “Remote site:” window, select all files (CTRL-A), right-click and choose “Download.” The PHP files will start downloading into the new directory you created, preserving the file structure of the server. This should be pretty fast, because you’re only downloading text files.
8. Once the download is complete, open an Explorer window and navigate to the directory on your computer where the PHP files are located. Right click and choose “Open with…” and then navigate to the Notepad++ directory and choose the file called “notepad++”. Select this as the default for opening all PHP files.
Notepad++will open with all the files you’ve selected in separate windows. Flip through the windows until you find one containing the rogue code at the top.
9. Select all the characters between the first two occurrences of the “<?php” characters. Include trailing spaces.
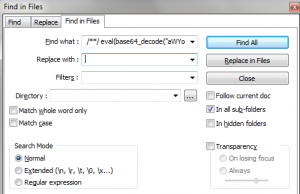
In Notepad++, choose “Search –> Find in files…” The dialog box that pops up will look like the one below. The text you selected should already be inserted into the “Find what :” field. Delete anything in the “Replace with :” field. Then choose the navigation button to the right of the “Directory :” field and navigate to the folder containing your PHP files. Click OK. The program will respond with the challenge of “Are you sure you want to replace all occurrances [sic] of…” Click OK. Notepad++ will churn away for a few seconds and then show you how many files it has changed. The number may astound you.
10. If all has gone well, you should still see part of the rogue code in the window in front of you. This is because Notepad++’s “Find what :” field can’t hold all the characters you need to replace. So you’re going to have to run another find and replace. Simply select the remaining bad code and repeat the previous step to find and replace all incidents in the files. If all has gone well now, the file in front of you should be clear of all bad code. Save that file and any files that are open in other windows and exit Notepad++.
11. Go back to FileZilla and upload all the PHP files, being careful to choose the same directory from which you downloaded them originally. When the challenge box pops up, specify “Overwrite” and “Always use this action.”
Try to open your site again. It should be back to normal. If it isn’t, upload the bad files you had stored in a separate directory and try something else, because this obviously wasn’t the bug you had!
If the fix works, be sure to change your database and WordPress passwords. And let me know either way whether this did the trick!

Pingback: A Quick Fix for the Latest WordPress Virus | paulgillin.com | WordPress World
Pingback: Which of these events is the most likely to cause a widespread influenza outbreak? | Personal health imformation
Pingback: Fredericton Web Design :: 27 Great WordPress Articles I Almost Missed :: Christopher Ross
This was exactly what I needed today! I set up a WP site for a non-profit last year, and they suddenly contacted me last week to say they needed emergency help to resolve a virus (among other issues). I followed these steps and the issue is now resolved! I have some clarifiers for other who run into this issue:
Step 6: “You actually won’t see those folders at the moment because your filter is on” Actually, you will see the folders because the author has correctly told us to ‘uncheck the box that says “Filter applies to: Directories.”’ in step 4
I also found it was very important to not only remove everything “within” the PHP tags, but in fact to remove the entire first line of code, including those tags and the carriage return. As noted here, you will need to do two replaces. In my second “replace”, I selected everything that was left, including the ”
<
and replaced it with "<" instead of blank. This way,I knew I got rid of the line entirely. The author mentions to include all trailing spaces, but I hadn't done so properly the first time as the php tags were not mentioned.
Good luck to others, and thanks again for sharing this solution!
Ive found a new wordpress virus here :https://turko.ca/wordpress-infected-virus.html
Just made a post about it.
Pingback: Wordpress Injection Issue | Welcome to my geekblog
Great write up. I have a few questions though. What were some of the signs and symptoms that your site was infected? Did you download some of the files and scan them with and antivirus or an antimalware program? One of my sites have been getting hit with a lot of spam lately and I was wondering if it’s possibly infected with malware.
Malware shouldn’t cause an increase in spam. More likely you were simply discovered by the spammers and they’ve turned their guns on you. Try Akismet to relieve the torrent.
This particular bug installed a trojan horse on a visitor’s computer, masked as antivirus software. The bug hit my computers first and then a few people e-mailed me to complain that it had happened to them. Also, the WordPress dashboard was corrupted.
@Paul
I have Askimet installed on my sites but they were still getting hit. After I dug around a bit I came up with a plug-in that adds a captcha to my site. In order for someone to comment they have to fill out a simple math equation. This has since stopped the comment spam.
What loop hole in WordPress is letting this virus to go in and modify files ?
Appears to be a password hack, probably from a keylogger. The problem appears to start with malware that loads under the guise of being anti-virus software. I’m guessing it picks off WordPress passwords, because two sites that I rarely update weren’t affected, while three that I tend regularly were hit.
3 of my sites have been hit and one of my friends too, infuriating. we’re all on different hosts and some had the problem you wrote about and some had the htaccess file changed too (by adding a redirect to a Sudan government website, south dafur? weird). I got downloads then removed and reinstalled WP with a new database, seemed to sort it but it’s a pain. wish i’d known about this before, great write-up!
I am totally fed up with wordpress virus on my client’s websites. If your solution works well, i will be thankful to you.
I downloaded a free template from https://www.templatelite.com/ and the alphanumeric code pictured above is written in the template files already. It is in the template.php file, so it’s not something that infected a file, but something that was already in the coding before even being downloaded. A friend of mine and I were decoding and with each base64 decode came up more code and more code and more code until we gave up trying to decipher this thing. It appears who created the templates had this “virus” pre-installed.
Thank you very much for this easy-to-follow explanation.
I discovered code specifically targeting google bots.
Using the method here, I was able to find many infected php files and it has saved me from having to re-install my site.
Thank you for saving me a lot of time. I had no idea you could filter the view in Filezilla. Again, another excellent time-saving bit of advice!
I’ve had trouble with an annoying virus also infecting php files. After reading this guide:
https://marketingsiden.dk/how-to-remove-god_mode_on-wordpress-virus/
I realized there was a hole in timthumb.php.
I wrote a php script to remove all the malicious codes from wordpress files. You can find it here : https://www.tahapaksu.com/wordpress/about-costabrava-hack-and-some-fix
Note: the base64 code may vary so you can change it inside the file, then run it.